Weapons called winder are added so that the launch direction is curved.
Contents
Previous tutorial
Duplicate Weapon object
First, clone the Weapon object that is a child of Enemy3 from Hierarchy.
- Right-click on “Enemy3/Weapon” in the Hierarchy window.
- Select “Duplicate” from the menu.
- Renamed to “Weapon 2”.
Open Weapon2’s ArborFSM in Arbor Editor.
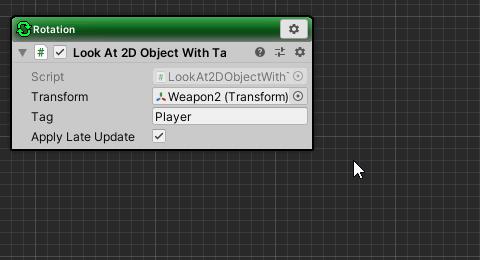
Delete LookAt2DObjectWithTag
Delete LookAt2DObjectWithTag from the Rotation state in order to stop the player’s aim.
- Click the LookAt2DObjectWithTag setting icon in the Rotation state.
- Select “Delete” from the menu.
Add TweenRotation
Add a TweenRotation to gradually change the orientation.
- Click the Rotation state setting icon.
- Select “Add Behaviour” from the menu.
- Select “Tween > Tween Rotation” from the behavior selection window.
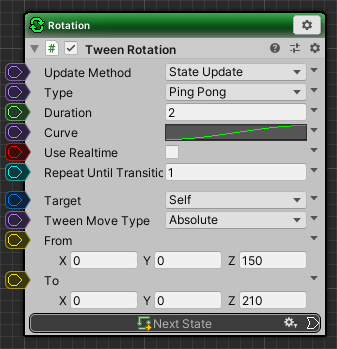
TweenRotation settings
Weapon’s angle is set between 150 degrees and 210 degrees.
- Change Tween Rotation of Rotation state as follows.
| Type | PingPong |
| Duration | 2 |
| Curve | Select EaseIn & EaseOut preset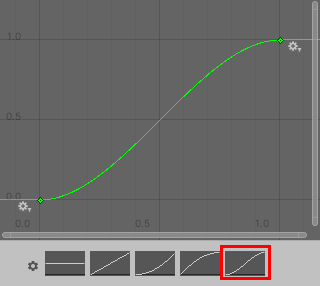 |
| From | 0, 0, 150 |
| To | 0, 0, 210 |
Shorten the firing interval
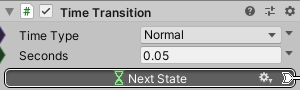
Change the TimeTransition in the Shot state to shorten the firing interval.
- Change TimeTransition of Shot state as follows.
| Seconds | 0.05 |
Adjust the launch direction
In this state, since the gap between two bullets launched at the same time is narrow, adjust the launch direction to widen the gap.
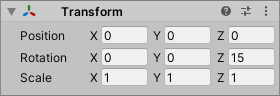
ShotPosition1
- Select “Enemy3/Weapon2/ShotPosition1” in the Hierarchy window.
- Change Transform as follows in the Inspector window.
| Rotation | 0, 0, 15 |
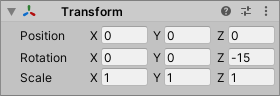
ShotPosition2
- Select “Enemy3/Weapon2/ShotPosition2” in the Hierarchy window.
- Change Transform as follows in the Inspector window.
| Rotation | 0, 0, -15 |
Change the weapon used
Edit Enemy3’s Arbor FSM to change the weapon Enemy3 uses.
- Select “Enemy 3” from the Hierarchy window.
- In the Inspector window, click the first ArborFSM “Open Editor” button.
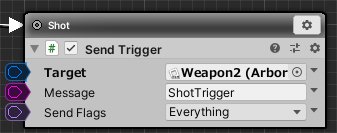
- Change the Send Trigger in Shot state in the Arbor Editor window as follows.
| Target | Weapon2 object |
Play Check
Let’s check the operation by pressing “![]() play button”.
play button”.
You can see that enemy bullet shots have been changed.